# AppSealing Setup Guide
This section describes how to request a license and download docker tarballs for AppSealing.
# Installation Steps for Onpremise version on Client Side
Setup 3 Linux servers (Ubuntu preferred) one for master node and two for worker nodes
- Hardware Requirement on each Node:
8GB RAM, 8 CPU Cores and 256 GB Disk Space
- Hardware Requirement on each Node:
Setting up the Kubernetes locally on the servers and install all the dependencies like Helm, kubectl and nfs-commons etc.
Setting up the NFS Server for Persistent Volumes.
Setting up Mysql and ELK Stack.
Update the Helm-charts with NFS, Mysql and ELK Endpoints.
Deploy the Appsealing On-Prem Solution
# Requesting AppSealing on-premise version.
To Use AppSealing on-premise version, customers must request a license first.
Customers should designate Android Package names and IOS bundle names to be sealed.
Fill in the form below, and send this form to your contact point please.
If the AppSealing Team creates deliverables with the customer’s request, a download link will be sent to the customer.
| Name | Description |
Package_Names | Android Application’s package names to be sealed. “*” can be used as a package name. e.g)com.inka.* , com.appsealing.* |
Bundle_Names | IOS Application’s bundle names to be sealed. |
# Download AppSealing
Use the download link provided by AppSealing Team
# Kubernetes Environment Setup
Setup with tarballs
First, download the docker tarballs into your host from where you are running the Kubernetes cluster.
Untar the docker tarball by using the following command.
$ docker load < docker-tarball.tgz
$ docker images ( You can see the image loaded into your system)You can upload this image to any docker registry. It might be your ECR, GCR, ACR, or some other docker registry where K8 can pick these images into the environment.
Update the YAML files with the images version and deploy the AppSealing on-prem version.
# DataBase Settings
AppSealing uses a “MySQL” server as a data source. using a script file provided by Inka will help set up a database.
Create a Db instance.
Make sure it is accessible from the Kubernetes cluster
# Import Database
Unzip db migration tool provided by AppSealing
Modify application-SVC.properties to access database instance
spring.datasource.url
spring.datasource.username
spring.datasource.password
Execute DB Migration Tool
- java -jar dbsync.jar --spring.config.location=file:./application-SVC.properties
# Configuring variables stored in the Database
AppSealing stores some credentials and other information in the database table.
AppSealing can support real-time configuration changes by using a database table. When the on-premise environment is ready. some configurations should be updated in the database table.
# Variables in was_properties table
| Parameter Name | Description |
GW_API_ROOT | Endpoint of API Server for IOS Sealing Service |
IOS_SQS_BASEURL | Endpoint for IOS reports on log-schedulers. Reports from mobile devices should be defined here. AppSealing supports only HTTPS protocol. |
SERVICE_SITE_URL | Endpoint for web console which can use actual sealing services and data services. |
SQS_BASEURL | Endpoint for Android reports on log-schedulers. Reports from mobile devices should be defined here. AppSealing supports only HTTPS protocol. |
URL_OF_ELK_SERVICE | Url of ElasticSearch cluster. Example: 4cea36c9e02e448592e386ac86879fb4.ap-northeast-1.aws.found.io (opens new window) |
USERID_OF_ELK_SERVICE | User Id for ElasticSearch Service |
USERPWD_OF_ELK_SERVICE | Password for ElasticSearch Service |
# Deploying AppSealing on K8S cluster
This section describes how to deploy docker images on the K8S cluster. Please, Make sure that docker images are loaded successfully from the docker tarballs.
# Check Docker image Path. Check Configuration files
Before Start Services on K8S, configuration files should be reviewed. If there’s any configuration error, AppSealing won’t be installed successfully.
Configuration files will be provided with docker tarballs at the time of delivery.
Here are some check items to be reviewed
Docker Image Path
If Docker images are staged in a private repository. update docker image URL
If Docker images are loaded in the localhost, update docker image path
HTTP Port Number
Volume Mount
# Configuration File List
| Parameter Name | Description |
adc | onprem-adc.yaml |
aos-datascheduler | onprem-aos-data-scheduler.yaml |
api | onprem-api.yaml |
ios-datascheduler | onprem-ios-data-scheduler.yaml |
log-scheduler | onprem-logscheduler.yaml |
sealing-server | sealing-server-deployment.yml |
internal-api | internal-api-deployment-with-service.yml |
Persistent-Volume | pvc.yaml |
Config-Map | configmap.yaml |
# Start Deployment
Before installing the AppSealing on-prem solution, we need multiple persistent volumes. We can have single persistent volumes or multiple persistent volumes. You can follow the below steps to provision a persistent volume.
You should have some persistent Volumes and create the persistent volume claims and update the same in helm-charts.
We will provide the helm charts for the appsealing on-prem solution and follow the below steps to deploy the product.
Install Helm 3 following the below URL, you can find the steps for your host machine. helm.sh/docs/intro/install/ (opens new window)
Untar/unzip the helm charts in some directory and go to that directory.
Update the helm charts with docker images and persistent volume claims.
Run the following command to install the appsealing on-prem version
helm list ( to check if there is any existing version of appsealing running or not)
helm install appsealing helm-charts (helm-charts is the directory which contains your helm charts and appsealing is release name)
helm upgrade appsealing helm-charts (To update any existing running version)
helm delete appsealing ( To delete any running appsealing version )
If there are any issues with configurations, error messages will be displayed. But most of the errors are caused by wrong configurations. Please contact us if the errors can’t be resolved
# Supporting HTTPS protocol
For the secure operation of the On-premise version. We recommend using HTTPS protocols for the api, and log-scheduler modules. To support HTTPS, any kind of Ingress controller or ELB is required.
Below are the redirection examples
| Module Name | example URL | Redirection port |
api | api.appsealing.com (opens new window) | 8090(default, configurable) |
log-scheduler | log-scheduler.appsealing.com (opens new window) | 8080(default, configurable) |
# Checking Pods/Service
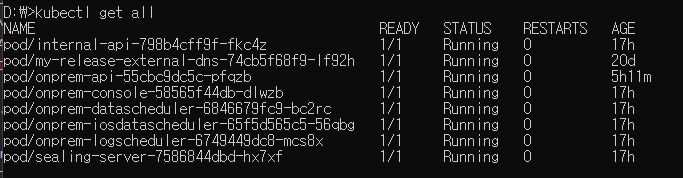
Use the kubectl command to check if Pods/Services are running correctly.
# Accessing AppSealing Web Console
When the installation is finished successfully, Visit Web Console with your browser.
An error message will be prompted if the web console fails to access the API server.